Linux Kernel Livepatch
Mitigate Linux kernel exploits
with Livepatch
Livepatch shrinks the exploit window for critical and high severity Linux kernel vulnerabilities, by patching the Linux kernel between security maintenance windows, while the system runs.
Livepatch provides security coverage for 10 years with Ubuntu Pro, and an additional five years with Ubuntu Pro's Legacy add-on, for a total of 15 years.
The benefits of Livepatch
Spend less time on unplanned work
Anyone that takes their security posture seriously applies critical and high security patches with urgency, outside their regularly scheduled patching maintenance window. This is work that impacts focus and distracts from goals and business objectives.
Livepatch reduces the unplanned work of installing Linux kernel security updates, making you more effective when managing Ubuntu systems.
Reduce downtime
Downtime is one of the major pains of every service provider, and it is unavoidable when deploying vulnerability fixes on the Linux kernel in the traditional way. That’s because the updated system needs to be rebooted, potentially disrupting Kubernetes, OpenStack, virtualized, or bare-metal workloads. Industry leaders avoid this problem and achieve high uptime by livepatching between scheduled maintenance windows.
Enhanced security
With early and cumulative patching of kernel vulnerabilities, Livepatch helps users maintain a strong security posture, and reduces the risk of exploits.
Follow organizational policy
Livepatch allows you to define your rollout policy and remain in full control of which machines will get updated and when, as well as provide updates to isolated network environments. System administrators can set a patching cut-off date and a patching delay on each machine, and uniformly secure groups of machines.
Ease of use
Livepatch is designed to be straightforward to set up and use, and patches are applied automatically after activation. Livepatch integrates with Canonical's web and API based Linux administration tool: Landscape.
Livepatch is used by









Kernel livepatching at a glance
When a high or critical Linux kernel vulnerability is detected a livepatch along with a Livepatch Security Notice are issued. Systems that enable the livepatch client will receive and apply the patch, after it is made available. The livepatch will provide new kernel code replacing the vulnerable one, and will update the rest of the kernel to use the new code.
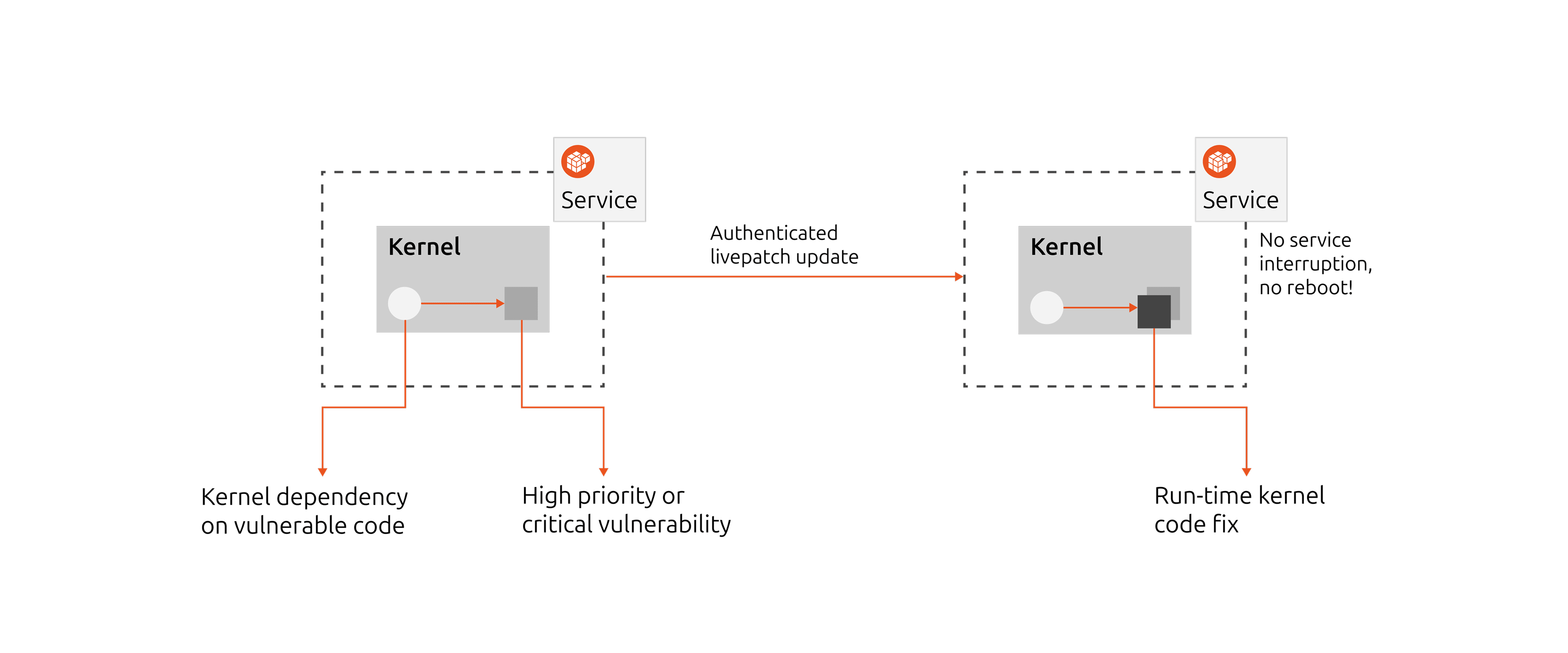
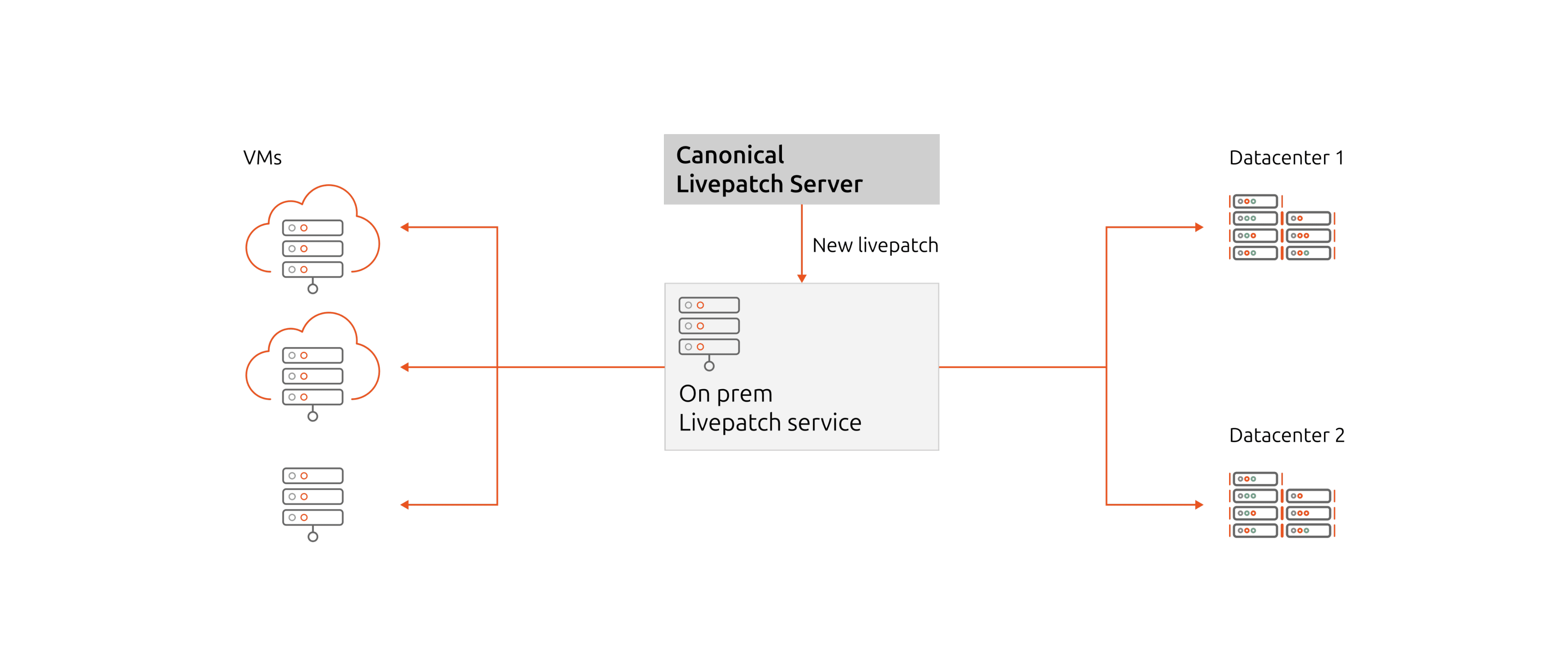
Livepatch on-prem overview
Livepatch on-prem is designed for air-gapped environments where Livepatch Client is unavailable to access security endpoints in Canonical's cloud. Livepatch on-prem can be updated with the latest patches, and Livepatch Client can retrieve the updates from Livepatch on-prem, instead of Canonical's cloud.
What our customers say

“Livepatch is a perfect fit for our needs. There’s no other solution like it, and it’s highly cost-effective. Manually migrating virtual machines, applying kernel updates, and rebooting took an average of 32 hours per server. Multiplied by 80 servers, that was more than 2,500 hours of work.”
Shinya Tsunematsu
Senior Engineering Lead
Tech Division, GMO Pepabo

“Livepatch is like a dream come true, both from a technical and a business standpoint. Our Ubuntu systems now rarely, or never, have to be rebooted. Service is continuous. That makes a big difference for user and customer satisfaction and loyalty.”
Masaaki Hirose
IT Platform Department
DeNA
Get Livepatch with Ubuntu Pro
Ubuntu Pro is Canonical’s comprehensive subscription for open source security, support, and compliance. Ubuntu Pro gives you access to a trusted open source repository, compliance profiles for the most stringent security standards, and up to 15 years of vulnerability fixes for your OS, infrastructure, and applications – as well as tools like Livepatch and Landscape that make security maintenance and compliance at scale easier and faster.
Free for personal use
Livepatch is available free for up to 5 machines, for personal use, or evaluation purposes.
Part of Ubuntu Pro
Get Livepatch with an Ubuntu Pro subscription from Canonical.
How to enable
the Ubuntu Livepatch service
1 Attach your subscription
sudo pro attach [TOKEN]Note: obtain the subscription token via the Ubuntu Pro portal.
2 Enable Livepatch on your system
sudo pro enable livepatchCanonical Livepatch resources
-
Documentation
-
Datasheet
-
Terms of Service
Frequently Asked Questions
Should every vulnerability be Livepatched?
Canonical Livepatch patches kernel vulnerabilities with critical and high Common Vulnerability Scoring System (CVSS) and Ubuntu Priority ratings. Canonical targets vulnerabilities that have security implications, such as privilege escalation or remote code execution, and are practical to patch safely in-memory.
Canonical Livepatch does not patch userspace libraries like OpenSSL or glibc, because that is the responsibility of unattended-upgrades or a systems management tool, like Canonical Landscape.
Can Livepatch trap me in a patched state?
Canonical Livepatch prevents the risk of instability by providing cumulative patches instead of stacking incremental ones, which makes rollbacks unnecessary in practice.
Just like every Ubuntu kernel package, Canonical runs every Livepatch through the same testing and rigor. Each patch is tested cumulatively with previous patches, on real hardware, without emulation. Livepatch Client downloads a single cumulative patch for the running kernel. In practice, the failure rate of Canonical Livepatch deployments is vanishingly small, and for Canonical Livepatch, reboots remain the safest and most sensible rollback path.
Is Livepatch a substitute for upgrade and reboot?
Canonical Livepatch is not a replacement for rebooting. It is a tool that gives you more control by preventing unscheduled reboots. Reboots cleanly flush accumulated state inconsistencies from memory leaks, hung file handles, and other problems that could fester with long uptime. Eliminating reboots would expose any operating system to these inefficiencies over time. Trying to avoid all reboots results in incomplete security patching coverage, and leads to fragile patching strategies that involve service restarts and error prone dependency tracing. Scheduling reboots ensures a guaranteed clean slate.

